The most important new name in disruptive cybersecurity tech you’ve never heard of
—Canada’s Qnext Corp. quietly turns heads with its award-winning data security solution FileFlex® Enterprise, the new world benchmark in Zero Trust Data Access and Sharing that has one big job: to protect against unauthorized remote and in-office entry to company files and folders—
TORONTO ON – As vital infrastructures and large-scale enterprise continue to grapple with raging cybercrime around the world – from food to oil, hospitals to financial and academic institutions, and so many more — a Canadian security developer recently recognized as a Red Herring Global 100 Disruptive Technology Innovator is advancing the marvels of data access and sharing with a seamless plug-and-play for large enterprise that protects data in files and folders. It is the undisputed next generation of data armor in the Zero Trust architecture network security model that trusts no one on the outside or the inside of an organization’s global hybrid network.
It is no secret that this architecture is fast becoming the data security solution for large-scale enterprises, set against the backdrop of President Biden’s recent order to transition the U.S. government from VPN to Zero Trust’s global gold standard security (Executive Order in support of a zero trust approach to security). Businesses across the expanding hybrid global workplace are recognizing the immediate need to better protect their networks and data.
Anthony DeCristofaro, president and CEO of Qnext Corp., the award-winning developer of FileFlex Enterprise, the world’s only Zero Trust Data Access and Sharing platform says, “to protect an entire organization from breaches, you need to do more than secure your network and application access. You need to secure your data.” Last year alone, there were more than 2,000 ransomware attacks on U.S. companies and local governments, and they are growing more sophisticated every day.
Qnext Corp. has global partnerships with Microsoft, Intel, Hewlett-Packard Enterprise (HPE), and NEC Platforms.
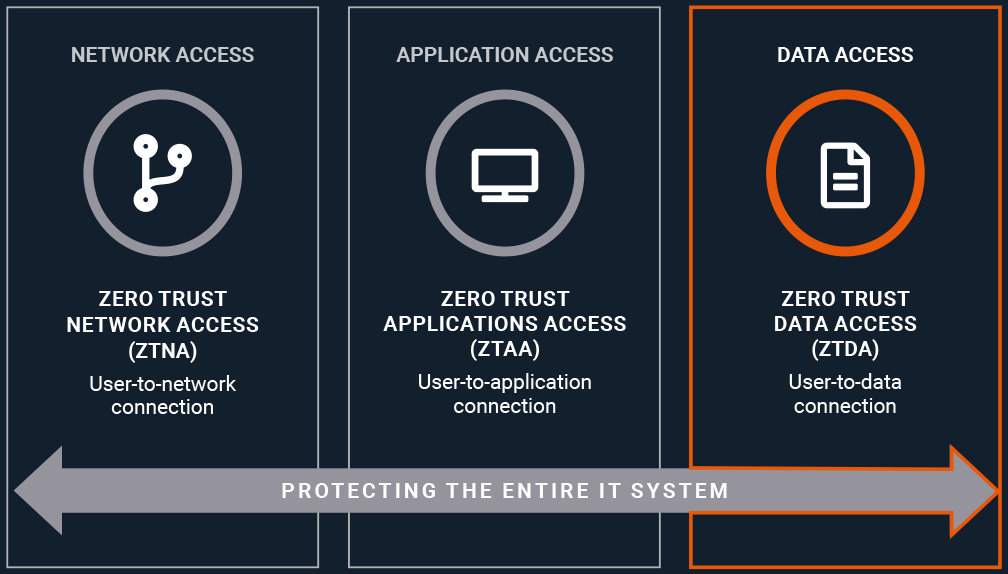
Zero Trust is about “verifying, every step of the way, how people access data, whether it’s through an application or device,” says Forrester Research analyst Steve Turner. Running in tandem with Zero Trust Network Access and Zero Trust Application Access, Zero Trust Data Access and Sharing protects data in files and folders like no other security model.
Remote work presents new data security challenges – even for top-notch VPNs
According to DeCristofaro, a reliable VPN will substantially lower a business’s chances of being hacked. “However, if the past 18 months has shown us anything, it’s that even the most highly rated VPNs are far from foolproof. VPNs have been under constant assault since the pandemic began.”
DeCristofaro cites one sophisticated attack that compromised more than 900 Pulse Secure enterprise VPN servers, enabling the attackers to gain access, steal account credentials, and exfiltrate other sensitive data belonging to victim organizations. “Pre-COVID, you had maybe 10% of employees using an organization’s VPN one or two days a week. Now, you likely have 90% of employees or more using an organization’s VPN five days a week. Each one of these employees creates a new point of vulnerability.”
Just one compromised employee using a company’s VPN can lead to having an intruder. “This is a company’s worst nightmare, and an attacker’s dream come true.”
How Zero Trust works
No user or machine within or beyond an organization’s firewall should ever be trusted, DeCristofaro emphasizes.
Unlike VPNs, which typically grant users access to large portions of infrastructure, a Zero Trust platform requires user verification each and every time access is requested. This ensures individuals can only gain access to the assets and applications they need. As an added measure of security, all access attempts and actions — like editing, copying, moving, and downloading — are tracked.
Like users, devices must also be authorized, and any device trying to access a network is automatically monitored in real-time. By permitting neither users nor devices to access an infrastructure freely, an organization’s sensitive assets are better protected.
The way forward, according to research
According to Gartner IT Research, “by 2022, 80% of new digital business applications opened up to ecosystem partners will be accessed through zero trust network access,” and 60% of enterprises will transition most of their remote access VPN solutions to Zero Trust by 2023.
Unlike VPNs, DeCristofaro says platforms that operate with Zero Trust assume that security breaches happen – “and rightly so.” He points to the May 2021 Colonial Pipeline breach, in which the fuel operator responsible for carrying 2.5 million barrels of fuel per day was temporarily shut down after being held for ransom by cybercriminals. “This, combined with similar cyberattacks on SolarWinds, Microsoft Exchange, and others, may be what prompted The White House to issue an executive order in support of Zero Trust.”
Now being adopted by the U.S. Department of Defense
“That’s how secure it is,” says DeCristofaro. “The ideal solution should be built from the ground up to apply it to networks, applications, and data. FileFlex Enterprise is the only data security solution of its kind and the most comprehensive platform for organizations that are ready to up-level their security around hybrid access to files and folders from the old-school perimeter-based model to Zero Trust.”
Remote work is here to stay
Adversaries know this and they are looking for ways to exploit any and all security vulnerabilities.
Pivoting to a security infrastructure or enhancing a company’s existing Zero Trust initiatives to facilitate fast, secure, and collaborative sharing is the smartest step towards protecting organizations going forward.
About Qnext Corp.
Qnext Corp. (“Qnext”) is the award-winning, innovation company behind FileFlex Enterprise, the industry’s first Zero Trust Data Access (ZTDA) and Sharing platform for today’s global and diversified hybrid workforce. FileFlex Enterprise has created a new enterprise-scale technology service that unifies the access, security, and governance of data storage across multiple environments using a Zero Trust architecture designed to support today’s Hybrid-IT enterprise infrastructure. The FileFlex Enterprise platform also integrates with Intel SGX secure enclave technology. Qnext has begun building a global distribution network of security-focused partners and is a partner with NEC Platforms, Microsoft, Intel, and Hewlett Packard Enterprise (HPE). At Qnext, disruptive products are the passion, demonstrated in the details. For more information visit https://bludis.fileflex.com/.
####
For more information, images, or to book an interview or Zoom segment with Anthony DeCristofaro, please contact Susan Willemsen or Margo Rapport at The Siren Group Inc. Email: susan@thesirengroup.com or margo@thesirengroup.com. Tel: 1-416-461-1567 or M: 1-416-402-4880/1-416-895-5672. www.thesirengroup.com, @thesirengroup.