How to Meet NIST Guidelines for Zero Trust for Remote Data Access
The National Institute of Standards and Technology (NIST) has produced NIST Special Publication 800-207 outlining Zero Trust principles and guidelines that can [...]
DETAIL
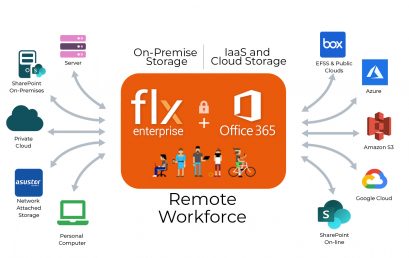
Key Benefits of Extending Office 365 with FileFlex Enterprise
FileFlex Enterprise extends the functionality of Office 365. It provides users remote access, sharing, and collaboration of Office 365 files located anywhere [...]
DETAIL
Extending Office 365 Functionality into a Hybrid-IT Infrastructure
The challenge comes when you want to access or share files stored on your hybrid-IT infrastructure other than on your own OneDrive [...]
DETAIL
How to Enable Your Remote Workforce with Zero Trust-By-Design
Organizations have been depending on the use of VPNs, but VPNs provide a direct, trusted connection right past your perimeter defenses and [...]
DETAIL
How to Mitigate Spear-Phishing via FileFlex Enterprise Zero Trust
How to Mitigate Spear-Phishing via the FileFlex Enterprise Zero Trust Platform FileFlex Enterprise is a remote access and sharing platform built from [...]
DETAIL
FileFlex Enterprise is the Best Alternative to Varonis DatAnywhere
Varonis DatAnywhere will enter End of Life (EOL) in February 2020. That means that organizations that use DatAnywhere need to look for [...]
DETAIL
The CLOUD Act and the Importance of Keeping Data On-Premises
The U.S. government has announced its first bilateral agreement of the CLOUD Act with the U.K, This agreement will allow the U.K. [...]
DETAIL
What is Centralized Cloud vs Decentralized Hybrid-IT?
The FileFlex decentralized hybrid-IT zero-trust computing architecture differentiates it from the centralized model used by all other file remote access and sharing platforms. [...]
DETAIL
How to Prevent Secret Data Exfiltration Inherent to Cloud Storage Solutions
What is the CLOUD Act? SCA “warrant” recipients in the U.S. (U.S. based cloud providers) are now obligated to turn over evidence [...]
DETAIL
Addressing Cloud Computing Security Issues and Challenges – Part 3
Addressing cloud computing security issues and challenges is a complex subject and this series of blog posts barely scratches the surface. It […]